Security vulnerabilities are on the rise; as is the average cost of a data breach, at $4.45 million, a 15% increase over the past three years according to a joint Ponemon Institute and IBM report. One of the most prevalent sources of vulnerability is open source software (OSS), with the majority of software including open source components that are overlooked and often unpatched.
From Apache Struts (2017) and Log4j (2021) to curl (2023), the software industry’s reliance on OSS and the frequency of security exploits has set up a perfect storm for software supply chain security risk. The average number of open source items discovered per audit project by Revenera in 2023 was 2,500, up 14% year-over-year. So, what are organizations doing to combat these potential threats?
Governmental regulation to combat vulnerability
To start, regulatory bodies across the United States and the European Union are establishing requirements via the National Cybersecurity Strategy and EU Cyber Resilience Act, respectively, to combat the growing concerns of software consumers regarding the reliability and security of their applications.
Among the requirements of these regulations are transparency in the use of third-party OSS components, enhanced supply chain security, improved incident response and recovery processes, and mandates for software bills of materials (SBOMs).
What’s an SBOM?
An SBOM is a formal and queryable record containing the details and relationships of various components used in building software. In other words, it’s like the ingredients label for your software or the breakdown of your car’s various parts, where each ingredient or part is a component to the overall software application.
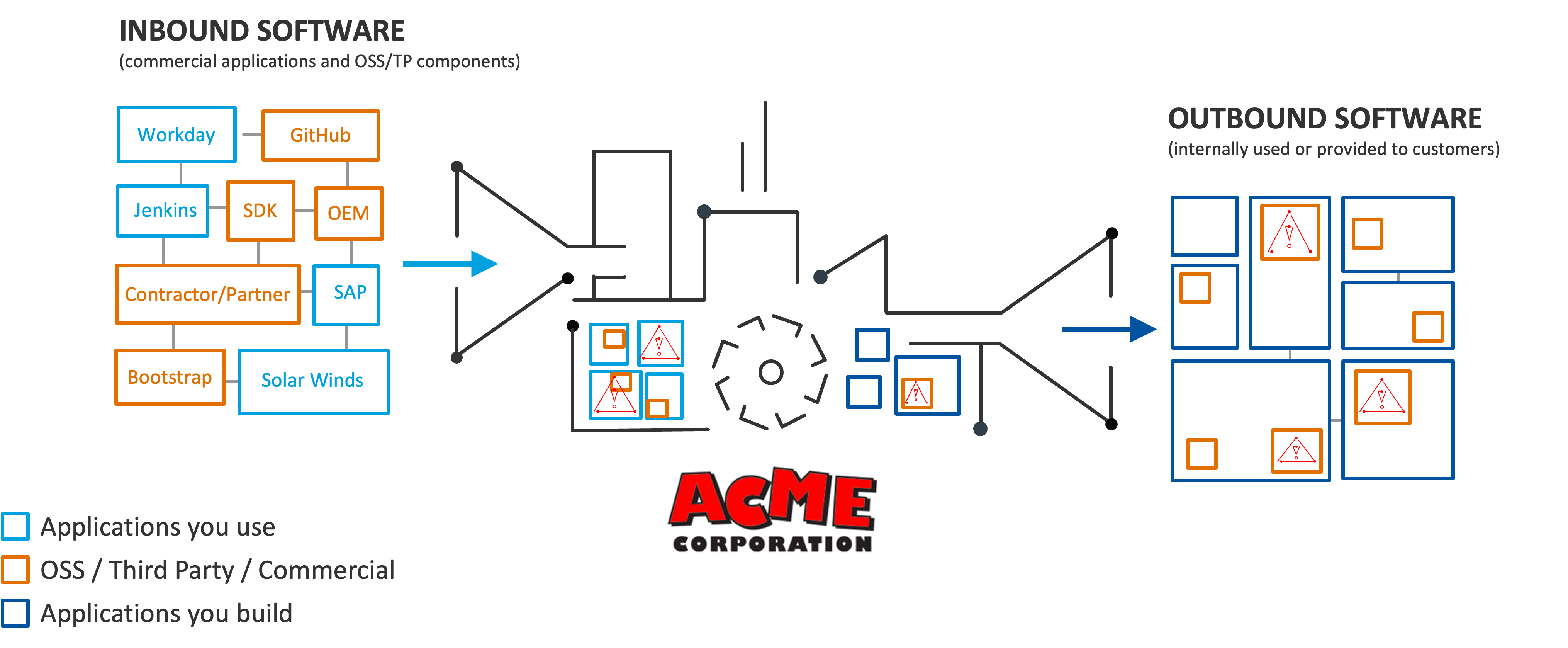
What can you do with an SBOM?
SBOMs exist for a number of reasons. As noted, concerns about application security make stakeholders want to know what is inside the software that their organizations use. Malicious actors may inject malware into open-source libraries, spreading vulnerability throughout the software supply chain as infected components get built into software applications. With so much OSS used on a per application basis, it’s difficult for many developers to stay on top of what OSS they used and which ones have newly discovered vulnerabilities from when they originally added it. In many cases, if an OSS library is working, developers will need a good reason to upgrade it, otherwise they’d prefer to keep what’s working as is.
With SBOMs in hand, security analysts, IT asset management, the legal department, development teams, procurement and other stakeholders can identify known threats that might be present in their software.
Cataloging the components across an organizations’ portfolio of applications allows impact assessment for newly reported security vulnerabilities to drive remediation work and patch updates.
Businesses and public sector organizations can also create SBOMs, so they can stay on top of the varied licensing agreements that arise with the use of open-source components. OSS components may be free, but they are not without contractual commitments or obligations. SBOMs help organizations understand which components comprise their products to assist with maintaining compliance with the incurred legal obligations.
With the aforementioned government regulations, and in some procurement policies, SBOMs can be required in order to remain compliant.
How do you build an SBOM management program?
Now that you know what an SBOM is and why it’s important, you may be asking, “How do I get started?” or “What’s important to know in managing SBOMs?”
First, start by determining where you intend to store and review your SBOMs—this may be as simple as a spreadsheet or a solution that can automate and facilitate the ingestion and reconciliation of data from multiple sources. When determining your storage space, it’s best to weigh the effort involved and the resources available to maintain continuous upkeep of an SBOM library for your various software applications across the business. It’s also important to reconcile industry standard SBOM formats, like SPDX and CycloneDX.
Next, assess your inventory. It’s imperative that you can tie your component data to vulnerabilities. Cyber risk causes brand and reputational harm in addition to considerable ransomware costs and potential downtime from an attack.
Finally, proactively address your identified issues. Reacting to industry security events is essential, but getting ahead is even more vital toward successful risk mitigation. A strong SBOM management program facilitates cross-functional collaboration and provides clarity into the software estate to reduce the chance of a breach and to prioritize remediation efforts.
IT Visibility delivers reliable SBOM management
We know SBOMs can be challenging for organizations to get started. That’s why Flexera supports ITAM and security teams with IT Visibility SBOM Management.
With SBOM Management, gain global views of all SBOMs across your organization. Assess the impact of SBOM components from OSS compliance to vulnerability risk and understand versioning for effective remediation.
IT Visibility
The business promise of your IT is huge. But it takes a complete, up-to-date view of your hybrid environment to make the most of it.
Flexera One IT Visibility delivers SBOM Management, so users can:
- Ingest and create a comprehensive list of all third-party components in a distributed or hosted app, including components from commercial off the shelf (COTS) and OSS components
- Construct SBOMs when third-party SBOMs are not delivered
- Establish a defined relationship between components (i.e. parent/child, dependency, related, etc.)
- Construct, ingest, and export SBOMs in industry standard formats, including SPDX and CycloneDX
- Provide additional reports about your applications’ security posture snapshot, including vulnerability disclosure reports (VDR) and vulnerability exploitability eXchange (VEX) reports.
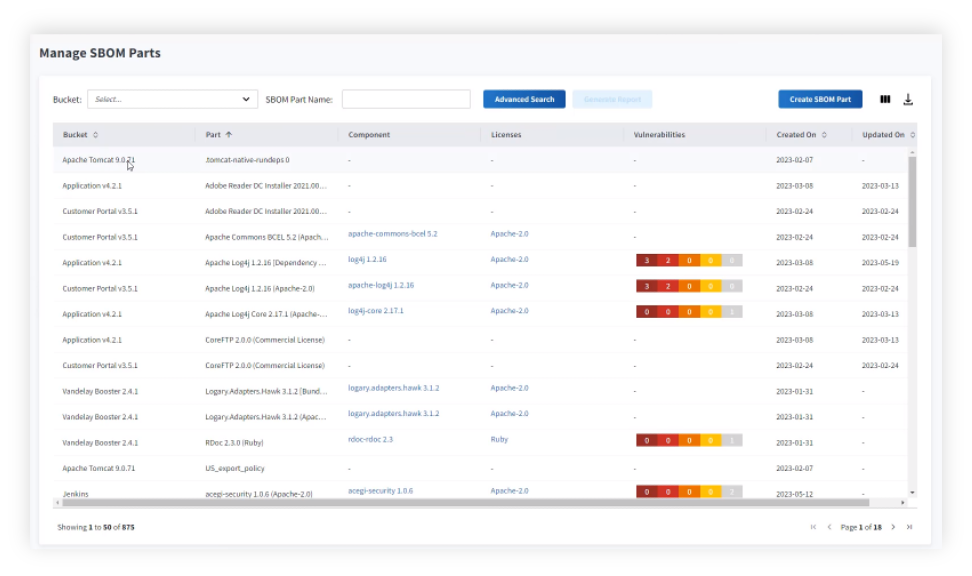
Manage SBOM parts in IT Visibility
While SBOM capabilities may be seen as a trend for some providers, Flexera’s solutions ensure that SBOM insights drive actionable strategies, making them part of a structured solution for software security. Join our free webinar to find out more about how SBOM Management can reduce risk and increase software reliability for your organization.