What is Digital Transformation?
IDC’s definition is:
Digital Transformation is the continuous process by which enterprises adapt to or drive disruptive changes in their customers and markets (external ecosystem) by leveraging digital competencies to innovate new business models, products, and services that seamlessly blend digital and physical and business and customer experiences while improving operational efficiencies and organizational performance.
IDC also defines their 3rd Platform, on which Digital Transformation is built, as being comprised of Mobility, Big Data / Analytics, Cloud and Social. Clearly, the cloud is a key aspect of both the platform and the digital transformation process.
But, what is the cloud? The cloud is (mostly) software! Its enterprise applications delivered via Software as a Service (SaaS). It is your own on-premises enterprise software being migrated to public, private or hybrid cloud environments. Of course, Infrastructure as a Service (IaaS) has a hardware-like component—instances of virtual servers that provide your basic compute capacity; but this is also something that must be managed by the IT Asset Management (ITAM) team.
Cloud adoption has been growing at a furious pace— a 21% annual rate. Cloud adoption accelerates the business by providing fast access to scalable IT services that can be highly cost effective—but only if you manage them properly.
Why are Software Asset Management and IT Security Management Technologies Key Enablers?
Let’s take SAM first. Software Asset Management has evolved to encompass not just management and optimization of your on-premises software, but also your cloud services. This includes both Infrastructure as a Service and Software as a Service. Management of cloud costs, maximizing the utilization of cloud infrastructure instances, and control of cloud sprawl are all critical elements of today’s SAM programs.
Managing costs is critical for cloud services—IaaS, PaaS and SaaS. With public cloud services such as Amazon Web Services (AWS), it can be difficult to have visibility of costs across the whole enterprise where there can be multiple accounts for different departments or cost centers. Your SAM tools need to provide this visibility and show you where you may be overspending on unused capacity. For example, you might have unused Reserved Instances which are costing you significant sums of money, as shown in the screenshot below (Figure 3).
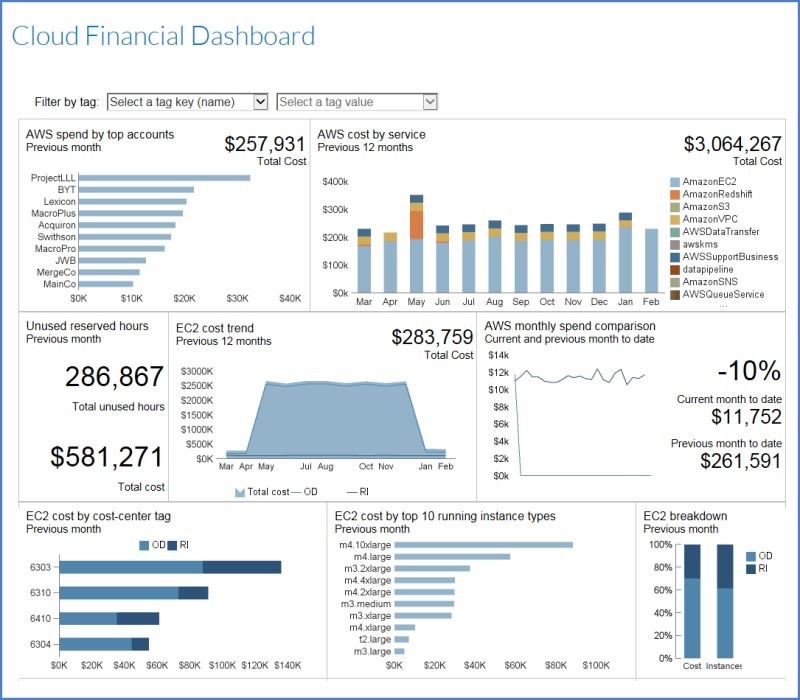 Figure 2: SAM Tool Financial Dashboard Showing Enterprise-wide Amazon Web Services Costs
Figure 2: SAM Tool Financial Dashboard Showing Enterprise-wide Amazon Web Services Costs
Similarly, SaaS subscriptions also require spend management. This means monitoring SaaS subscription usage and reclaiming and reallocating licenses for users that change jobs or leave the company. It also means selecting the right subscription plan level for your users, as in the case of Microsoft Office 365.
Also, as noted in the above referenced blog, the move to cloud infrastructure services also typically means that you are moving some of your on-premises software to the cloud, in which case, you still need to manage license compliance for that software. License compliance is still your responsibility, not the cloud vendor’s, in most cases. It’s also important to understand what software you have in your on-premises environment first, and whether you have license mobility rights to move that software to the cloud. These are all software asset manager responsibilities.
Controlling cloud sprawl, otherwise known as Shadow IT, is another important function for the IT Asset Management team. This can be accomplished with the help of an enterprise app store. The app store provides fast and easy access to authorized software and cloud services, reducing the likelihood that users and business units will go around IT to get these tools for the business.
Now let’s consider IT security. Living in a digital world means that your business is exposed to hackers that try to steal your data or intellectual property and/or take over your IT systems. That’s why cybersecurity is one of the top C-level priorities for most organizations. A primary “attack vector” for cybercriminals is the presence of software vulnerabilities in your enterprise software. There were more than 17,000 published vulnerabilities in 2016. Hackers develop exploit kits to take advantage of these software vulnerabilities.
18% of the 2016 vulnerabilities were rated Highly Critical in Secunia Research Advisories. These are vulnerabilities that must be remediated to reduce your security risk.
Application Readiness
The task of application readiness never ends. There are always new apps and updates. Flexera’s AdminStudio greatly reduces the burden and saves time.
The criticality rating is important because it allows your Security and IT Operations teams to prioritize the patching of vulnerabilities. This prioritization is key due to the large number of vulnerabilities disclosed every month. You need to know— ‘what are the most important ones to patch first?’
Software Vulnerability Management tools enable your IT security team to assess vulnerabilities in your IT environment, prioritize those vulnerabilities, and provide an efficient process for Security to work with the IT Operations team to patch those vulnerabilities to mitigate the security risk. In 2016, 81% of all vulnerabilities had a patch available on the day of disclosure – slightly lower compared to the 84.5% in 2015.
We can see that IT / Software Asset Management and IT Security Management are key enablers for successful Digital Transformation. And, IT/Software Asset Managers and IT Security Managers are critical players in this strategic business transformation process.



