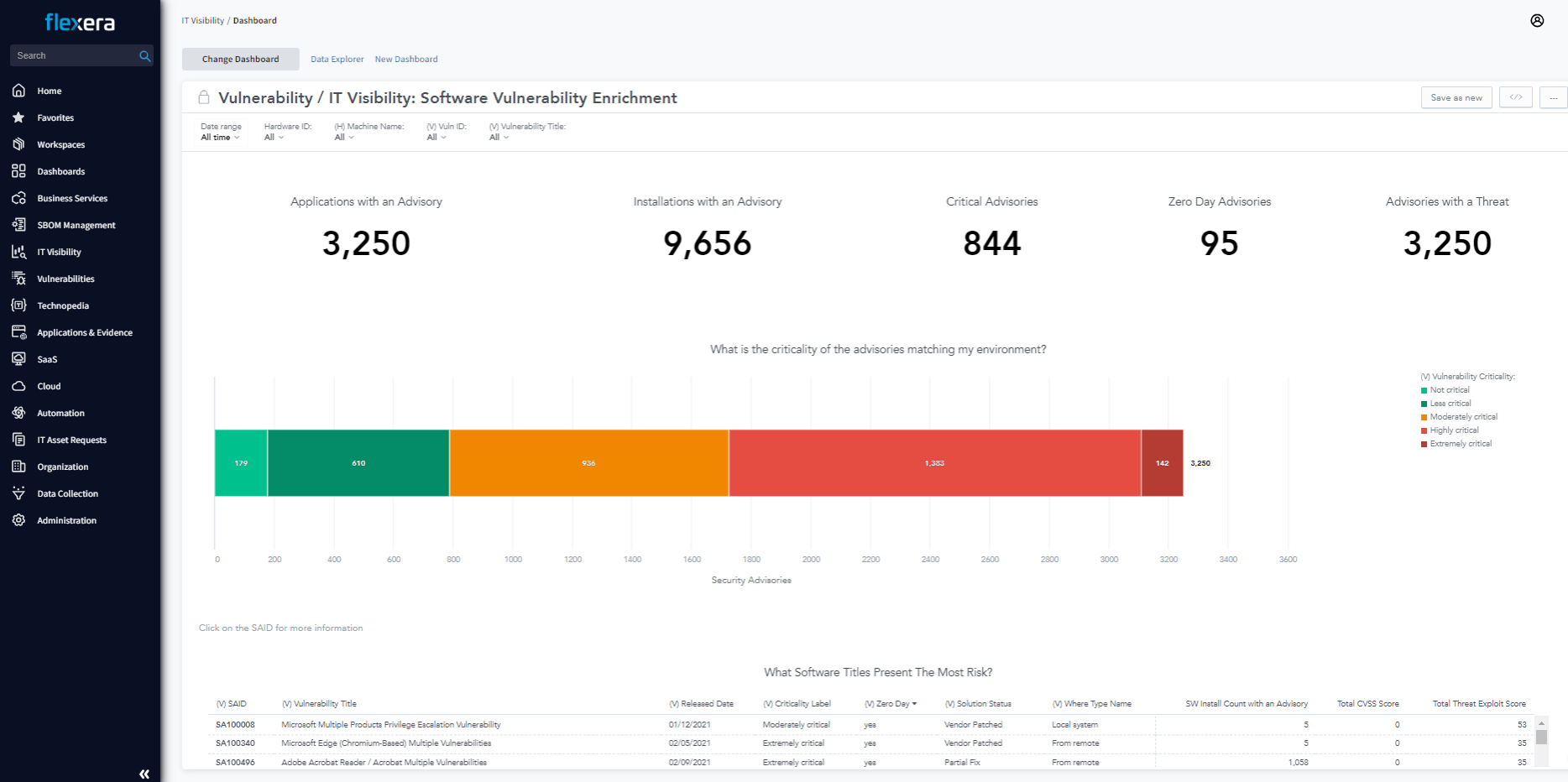
Software Vulnerability
Illuminate hidden threats in your digital landscape
Vulnerabilities often lurk unnoticed, posing silent threats to your IT infrastructure and business operations. Dive deep into the intricacies of your software inventory, uncovering potential risks and fortifying your defenses. Leveraging actionable insights from Secunia Research and other trusted intelligence, empower your organization to navigate the digital realm with confidence, ensuring robust security and informed decision-making.
Vulnerability insights
Multiple ways to identify software vulnerabilities
Benefits
Unlock the power of proactive vulnerability management
- Deeply understand and assess potential security risks.
- Achieve a comprehensive, holistic view of your IT landscape.
- Promptly detect and address software vulnerabilities.
- Make informed, security-conscious software choices.
- Stay updated with critical software lifecycle changes.
- Receive alerts on emerging vulnerability threats.
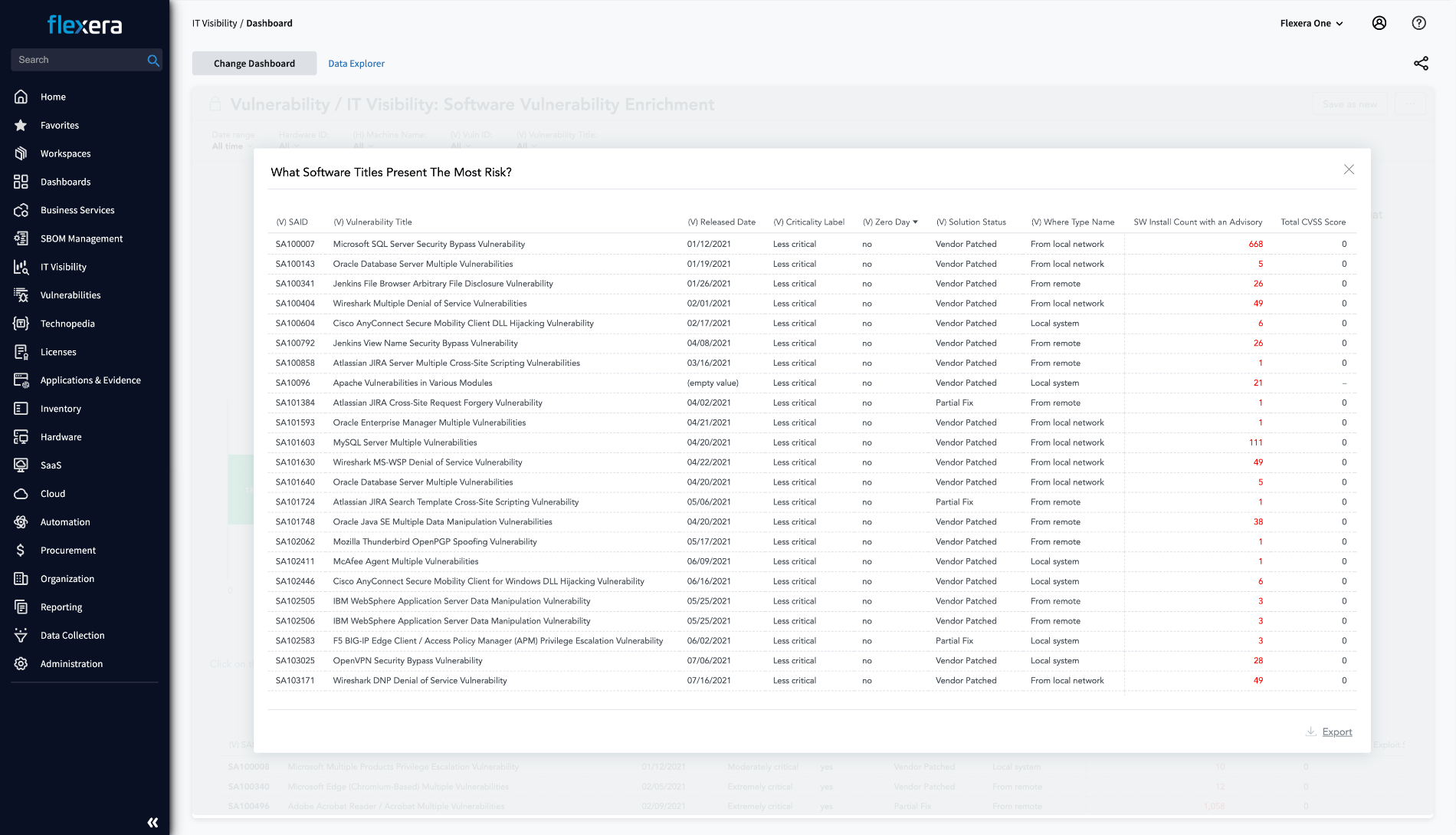
Featured details
Precision-driven vulnerability intelligence for enhanced security
Protect your IT environment from potential security breaches, compliance challenges, and escalating support costs with the unparalleled insights from the globally recognized Secunia Research.
- Comprehensive Data Coverage: Leverage data from both Secunia Research and NVD/NIST for a wide-ranging view of software vulnerabilities.
- Security Advisories: Stay informed with detailed insights into potential threats and their solutions.
- Prioritization: Address vulnerabilities based on criticality, threat, and potential business impact.
- Proactive Risk Management: Equip your organization with the insights needed to address vulnerabilities before they become threats.
Informing IT, Transforming IT
Industry insights to help keep you informed
Demo & Trials
Free IT visibility analysis
Confident your organization’s IT infrastructure is up to date and secure? Get a free IT estate analysis today and take the first steps towards protecting your business from the risks of IT obsolescence.
Datasheets
Software Vulnerability Enrichment Pack
The enrichment pack gives comprehensive vulnerability insights to fortify your IT environment. This minimizes your security exposures so you can focus more on top business priorities.
White Papers & Reports
Stay protected from software vulnerabilities with trusted IT visibility
You need a comprehensive view of your IT estate in order to address software vulnerabilities. Discover how complete visibility, collecting the right data and keeping it current can help you succeed in today’s hybrid IT world.
Events
Midwest Management Summit
May 5 - 9 | Bloomington, MN
MMS offers deep technical sessions on systems management and automation. MMS has over 100 sessions focused on ConfigMgr, Intune, Azure, Provisioning, PowerShell, and more, featuring world-class presenters from around the world. In addition to sessions, you will also have the opportunity to have in-depth Q&A sessions with presenters. And probably more important than everything else is the opportunity to network with your peers—this is something that is nearly impossible at large conferences. Network with peers, share war stories, brain storm, and share best practices.
Events
IAITAM Ace
May 7 - 9 | Las Vegas
The IAITAM Annual Conference and Exhibition (ACE) is the world’s leading IT Asset Management conference. At ACE, C-level executives, IT, Financial, and Legal professionals come together to explore the latest in ITAM and its impact on business operations, compliance, and profitability. IAITAM, the world leader in ITAM education, hosts over 2,000 attendees around the world at ACE every year. ACE fulfills the needs of the ITAM professional with over 100 educational sessions with ITAM experts, workshops, vendor interaction and networking opportunities.
Events
2024 Technology Intelligence Roadshow
May 16 - August 14 | Various Locations
Join us to discuss the growing visibility gap in IT, sustainability, SaaS sprawl, the intersection of ITAM and FinOps and more!