You can’t manage—or defend—what you can’t see
Enterprises aren’t strangers to cyber threats—but since Russia’s attack on Ukraine, more and more companies are seeking intelligence to shore up their defenses against growing threats. The Cyber Alert Level has been ranked Severe (Red) ever since the country’s military strike, and organizations like the Cybersecurity & Infrastructure Security Agency (CISA) have called on companies, organizations and authorities to expand their IT security measures.
Organizations can—and must—do more to protect their IT assets. Potential risks must be identified in advance and managed proactively, before the worst-case scenario even happens. It’s never been more critical to have comprehensive, data-driven visibility of all your software, hardware, SaaS and cloud assets. Only those who are able to see their entire IT landscape can appropriately defend it against threats. And in the context of the Russia-Ukraine conflict, IT and compliance leaders face significant challenges.
Which of my IT assets are currently located in Russia?
Russia is currently a sanctioned country. The EU, United States and other partner countries have adopted tough economic and financial sanctions against Russia in several tranches. Tech giants such as Google, Microsoft and Intel have already announced that they will stop doing business in Russia. Payment and credit card providers such as PayPal, Mastercard and Visa have also stopped their services.
To comply with these sanctions, IT organizations must first know which assets are in Russia. This impacts end user devices such as computers and tablets as well as data centers and servers that are used by Russian employees or partners.
Additionally, IT leaders should determine which software is running on these devices. For example, for license management and compliance it must be clear which licenses are available and how much leeway there is regarding usage guidelines. If the license falls under an enterprise-wide agreement, it can be transferred to another employee in the company and therefore continue to be used. However, if the license is subject to location-specific or legal entity-specific restrictions, IT managers often have no choice but to terminate them (true down).
Do I have Russian software running in my company?
Even organizations that don’t own any assets in Russia should subject their IT estates to a thorough audit. Applications originating from Russia should be assessed with a very critical eye. There are two reasons for this: first, the business relationship with the Russian provider may have to be terminated due to sanctions. Secondly, there is a justified concern that the applications could be exploited by Russian hackers. The cyberattack on SolarWinds and its massive impact on thousands of companies worldwide is still a terrifying reminder for many.
It goes without saying that organizations must take precaution. For example, since mid-March, security organizations like CISA have warned against the use of solutions from Kaspersky, a multi-national cybersecurity and antivirus provider headquartered in Russia. The antivirus software poses a considerable risk because it has extensive system-related authorizations and usually maintains a permanent, encrypted and uncheckable connection to the manufacturer’s servers. State-instrumented attacks and espionage activities via the software can therefore not be ruled out. Security agencies worldwide recommend replacing the Kaspersky applications with alternative products.
How safe is my IT estate?
IT security is precarious—regardless of whether a company operates in or sources its IT assets from Russia. Every organization should ramp up its security measures and take a closer look at its IT assets. Take inventory of what end-of-life (EOL) and end-of-service (EOS) applications and devices you have, and understand where vulnerabilities are found. Determine what upgrades and patches are needed, as well as which security gaps need to be closed.
Enterprises are often less prepared than they think they are. Many companies still use outdated computers, operating systems and applications that are in need of a security update. According to Flexera’s 2021 State of IT Visibility Report, two-thirds (67 percent) of companies still have hardware that has already reached its EOL/EOS—and 73 percent of companies still have EOL/EOS software.
What to do about it
Organizations who can count on automated IT asset management and discovery tools to answer these questions are already at an advantage. The first step for IT security is always about gaining IT visibility.
Flexera One visualizes your entire IT estate—from on-premises, to SaaS to the cloud. The holistic and centralized view of all your IT assets enables IT leaders to transform this intelligence into actionable outcomes. For IT security, this can be a fail-safe detection of risk. Flexera One’s IT Visibility is powered by Technopedia, the world’s most comprehensive and trusted source of hardware, software, SaaS and cloud product information on the market. Technopedia gives you the most complete IT asset intelligence available, with the ability to identify more than 4.5 million hardware and software products.
How it works
With Flexera One, now you can have the IT visibility you need to identify your IT threats. The contextualized data makes it possible to quickly and securely locate IT assets deployed in Russia by delivering technical data (e.g., host name, serial number, IP address) as well as master data related to location, cost center, organizational unit and which is assigned to individual devices or applications. On the network side, devices can be narrowed down to local and regional areas.
IT Visibility
The business promise of your IT is huge. But it takes a complete, up-to-date view of your hybrid environment to make the most of it.
Kaspersky may be a well-known Russian software provider, but it’s by no means the only one. If you want to know which Russian software may be running in your organization, you can search your IT assets by filtering by manufacturer or publisher in Flexera One. The result is a comprehensive list of all installed assets that match your criteria.
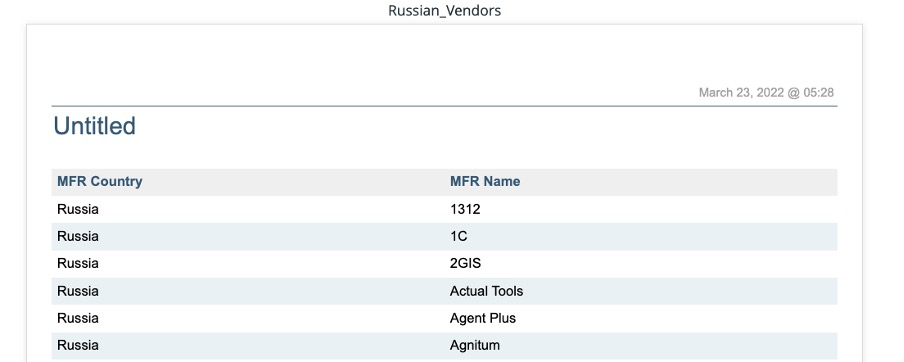
You can also get detailed reports on potentially dangerous IT assets. Flexera One enriches reports with market data such as EOL/EOS from Technopedia and provides threat scores and vulnerability advisories, which help you assess the security situation, prioritize upgrades and coordinate planning—including support costs.
Visibility of your hybrid IT estate is critical in all these instances. Today’s IT infrastructure is highly complex. With growing global threats and IT risks, you need comprehensive, complete visibility to take the best precautionary measures.