Software Vulnerability Research
Stay ahead with actionable vulnerability intelligence & research
Vulnerability breaches are common and costly for organizations. Software Vulnerability Research is the best way to prioritize the software vulnerability disclosures that matter to you. Rely on vetted vulnerability and threat intelligence to ensure timely awareness so you can react before it's too late.
Sprint ahead of software vulnerability threats
Verified, tested and validated by Secunia Research
Cover all applications and systems across all platforms
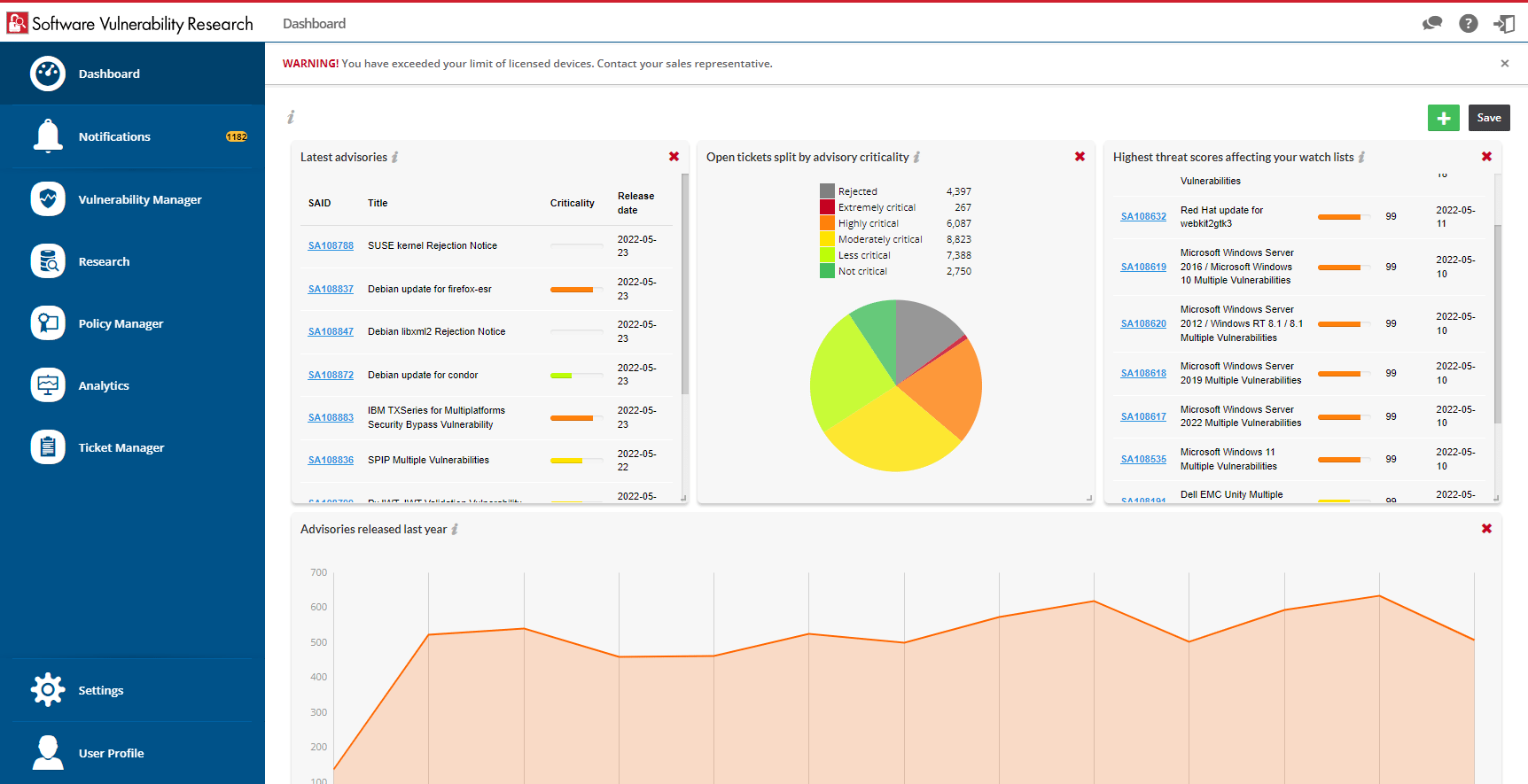
Knowing a vulnerability’s impact on your organization is paramount. Flexera Software Vulnerability Research provides access to verified intelligence from Secunia Research. Concentrate on vulnerability research, alerts and news relating to the products that matter most.
React quicker
Simplify and prioritize remediation efforts
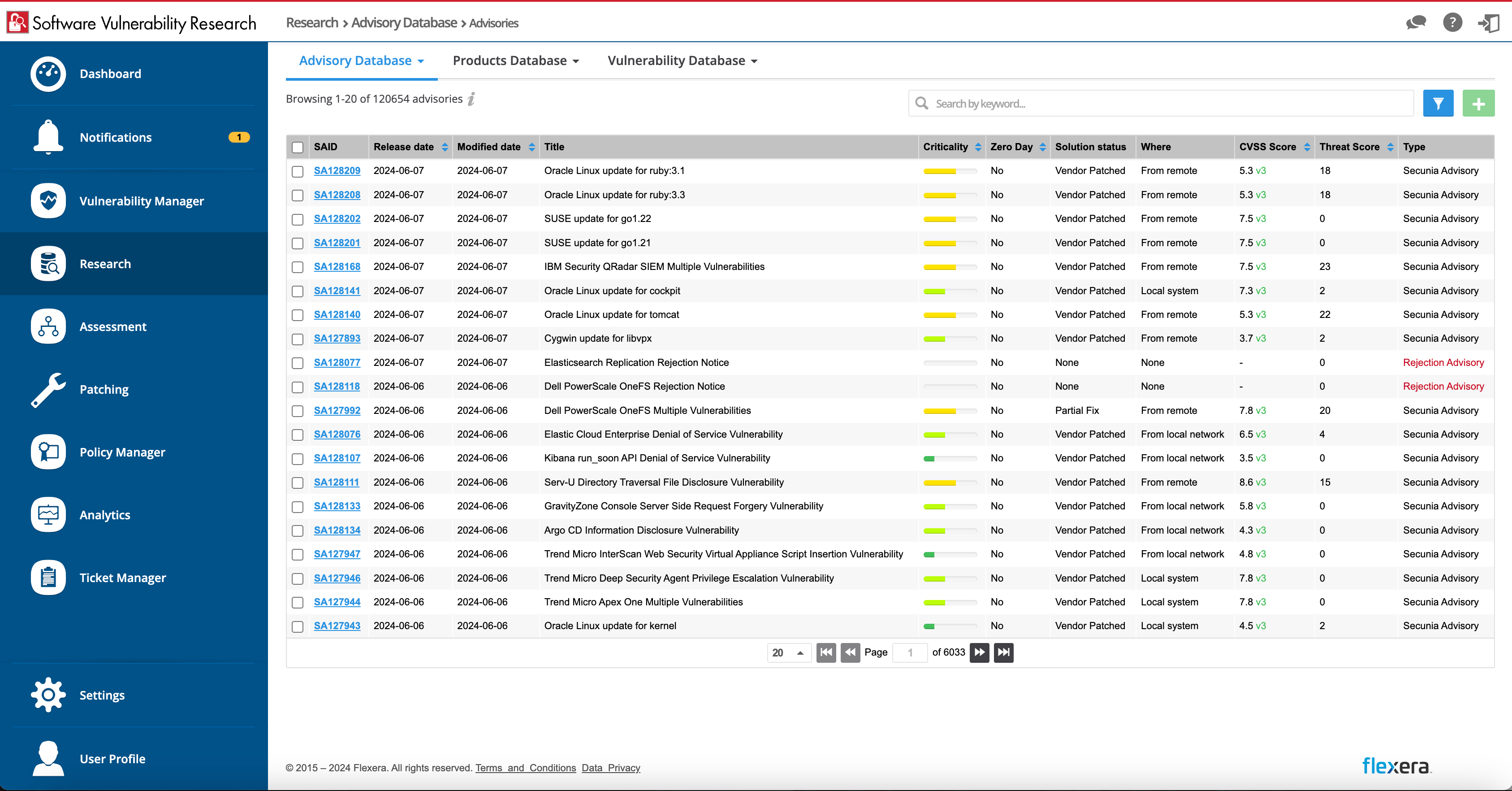
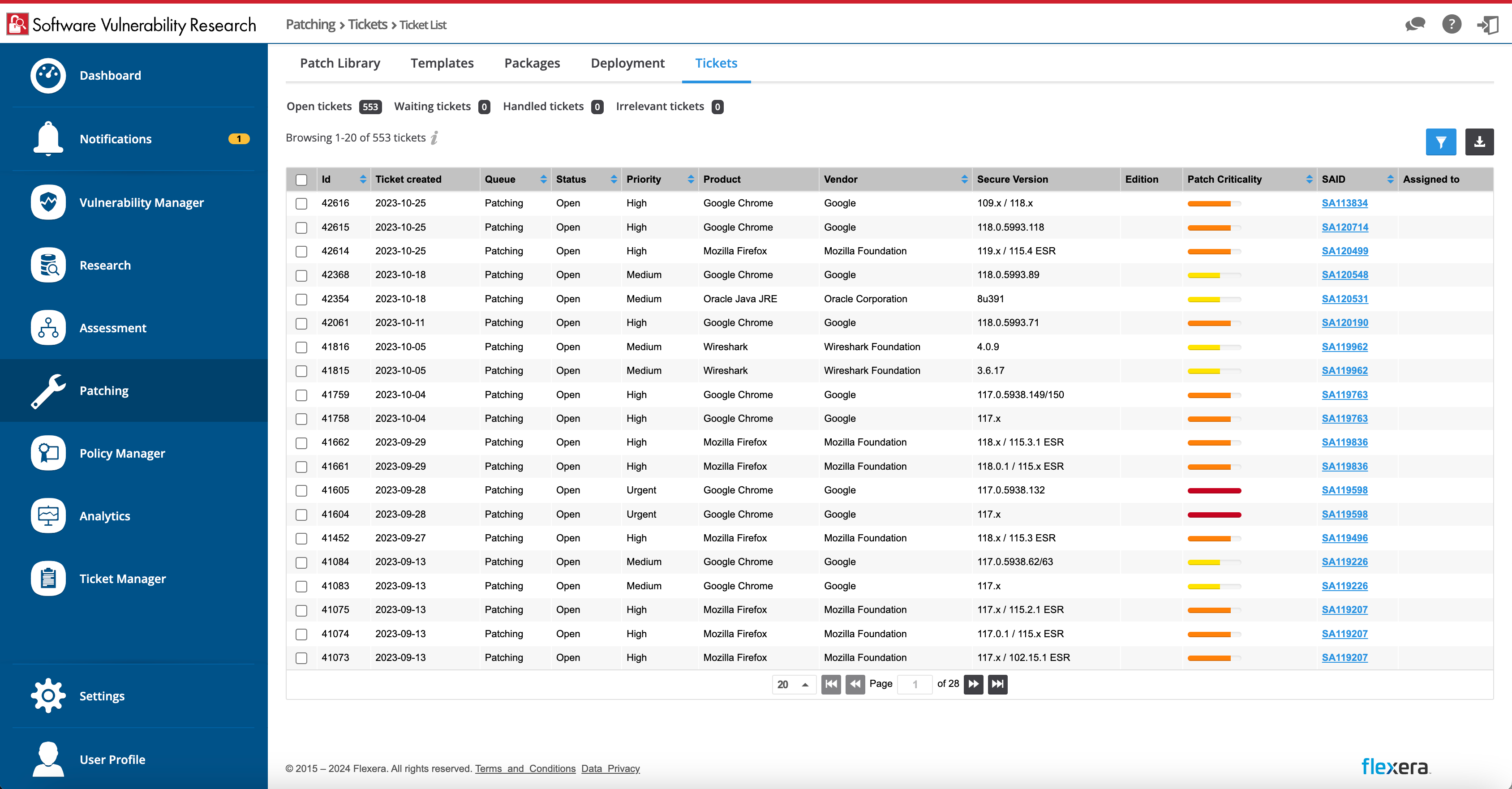
Remediation requires transparent processes and updates. Receive advisories, alerts, tickets, reports and visibility into security patches and software vulnerabilities.
Vulnerability in context
Leverage risk context and information
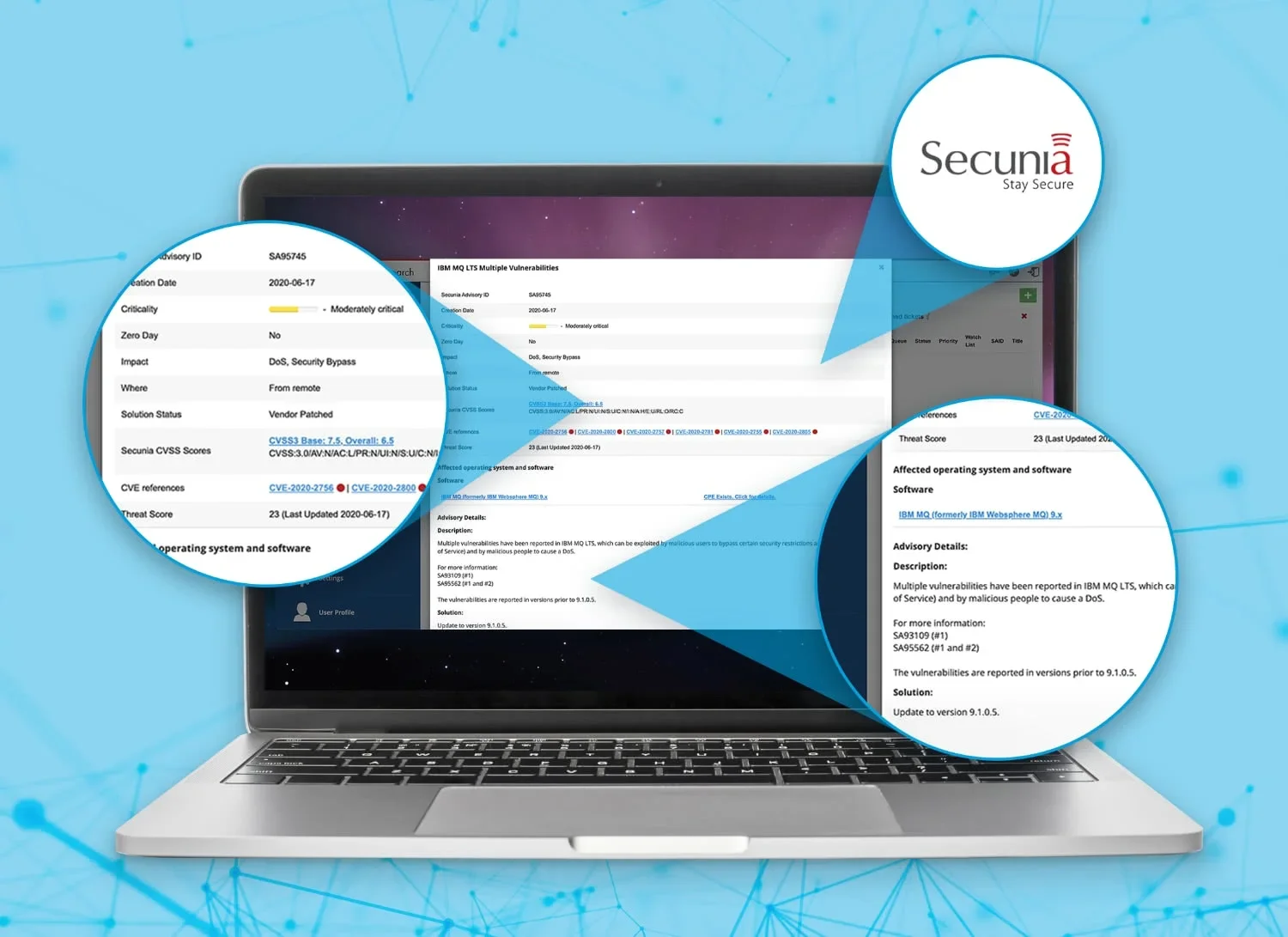
When it comes to vulnerabilities, context and depth of data are necessities for timely remediation. Unlike public sources, Secunia Research provides associations of known exploits to the CVEs within an advisory for a product. Threat scores are set by severity of the threat posed, quantified into categories of severity.


Take action efficiently
Mitigate the most critical and business-impacting threats first
A quick response is crucial to avoid costly breaches. Prioritization is driven by threat intelligence, workflows, tickets and alerts, and describes the steps to mitigate the risk of costly breaches. You stay in control and hackers stay out.
Stay in control
Gain coverage on all applications and systems
Providing timely alerts on potential risks empowers your IT team to manage proactively. Access trusted software vulnerability research covering the most third-party applications on the market. Keep unplanned events such as security exposures to a minimum and focus on executing your top business priorities.
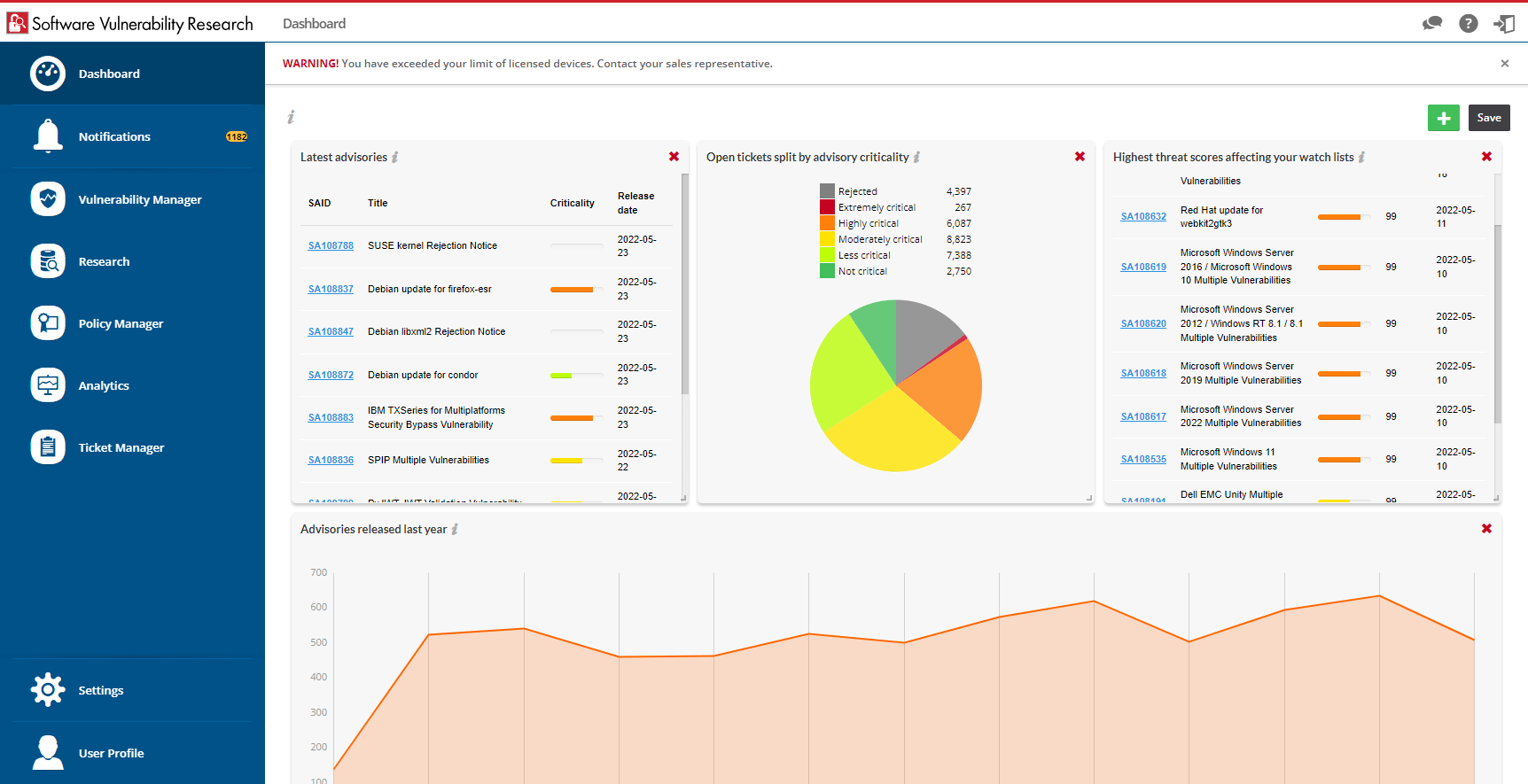
Software Vulnerability Research Details
Vulnerability Intelligence across the IT estate
- Get security alerts covering the applications and systems you care about
- Discover details about how software vulnerabilities may affect you, including their solution status
- Focus on what matters most based upon criticality, likelihood of exploitation, software vulnerability score and more
- Comprehend the likelihood of vulnerabilities with easy-to-understand threat scores for each along with amplifying details
- React more quickly thanks to software vulnerability alerts provided within one day of public disclosure
- Automate notifications and the creation of support tickets to ensure you’re alerting the right people to take action
- Optionally leverage APIs to integrate this valuable data into internal systems and processes
Frequently asked questions
Software vulnerability is a structural or design flaw present in a software application that can be exploited by attackers to compromise the security and functionality of the system, network or data with which it interacts. To learn more, visit our glossary here.
Implementing a comprehensive strategy to mitigate software vulnerabilities and safeguard your organization can present a number of obstacles. Common challenges include: resource constraints, complexity of systems, third-party dependencies, legacy systems, time sensitivity, skills shortages and regulatory compliance. Click here to learn more.
Informing IT, Transforming IT
Industry insights to help keep you informed
Know more than the hackers know
By proactively guiding prioritization and automating key processes, Flexera can help you close vulnerabilities before they develop.